
A professional losing a laptop or any mobile device has to face the humiliation, embarrassment and mockery. This is frustrating. A result of being careless at a coffee shop or airport can prove fatal with dangerous consequences. Of course, that laptop will have software and antivirus to prevent data breach but it isn’t enough to prevent data theft as hackers will find an override access into the file systems.
Without saying, it is obvious to protect all the confidential data securely and appropriately. The basic method of protecting your data is by password protection. It may be considered as a protection at a basic level, but in complex and advanced level, more secured and complicated data protection becomes essential. The reason why passwords can be bypassed is many employees use default password. Even if they don’t a unique password can be bypassed too because the password itself is data on a disk like every other data and with appropriate skill, it can easily be hacked.
There is no immediate action that can be taken post laptop or mobile device theft. The complications and the processes that arise later are frustrating and can lead the person to disappointment and depression. However, one way of having a control on the access of dataeven when it is not within the vicinity is by data encryption. A simple definition of data encryption is encoding data. It may sound easy, but it is complicated. In reality it’s a complicated process and requires deliberate planning.
DATA ENCRYPTION ALLOWS YOU TO MANAGE ACCESS OF DATA WITH FULL DISK ENCRYPTION
A full disk encryption is a complex codes to secure each n every minute data in your disk. The following image will explain the process and functioning of a full disk data encryption.
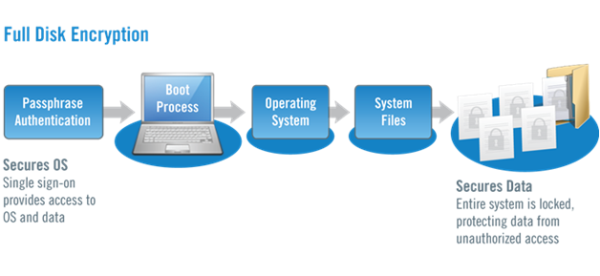 An illustration on how data encryption is secured.
An illustration on how data encryption is secured.
To secure any data with maximum security and prevent unauthorized access, the number of layers i.e. the number of pathways that lead to the main file systems should be maximized with each being more complex and stronger than the previous one. An authentication is required to access the first pathway followed by passing through operation system which ultimately leads to the system of files and each set of files has individual codes to access.
Another alternative would be by securing everything in cloud. Cloud computing (Please check out our recent blog post about cloud Managed Cloud Computing) is the latest trend which makes all the processes easier and simpler with IT Support Austin. Securing dataover the cloud and authorizing access only to trusted employees reduces the risk of data theft. With encryption, firewall and antivirus also play a crucial role in data protection.
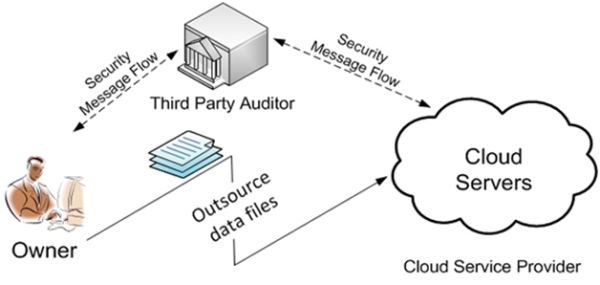
Functioning of owners and security message flow in cloud computing (protection).
For best IT support Austin solutions, considering the budget and the security of your precious data is essential. When it comes to Texas, Austin choosing a IT support and services becomes easier as the number of organizations providing standard and quality IT support Austin is few and choosing the best among these few is easy as that organization would be none other than Gravity Systems USA- IT Support Austin. From secure cloud computing tosecured network services, the services offered by Gravity USA is enormous and perfect.
For any data, protecting it securely becomes necessary and encryption, secured network file systems and cloud computing are some of those. Choosing the right IT Support organization is the key to securing your data safely.

_NO_BCS_bigger_weird_green_clear.png?width=100&name=for-website_large(save-at-500-tall)_NO_BCS_bigger_weird_green_clear.png)

